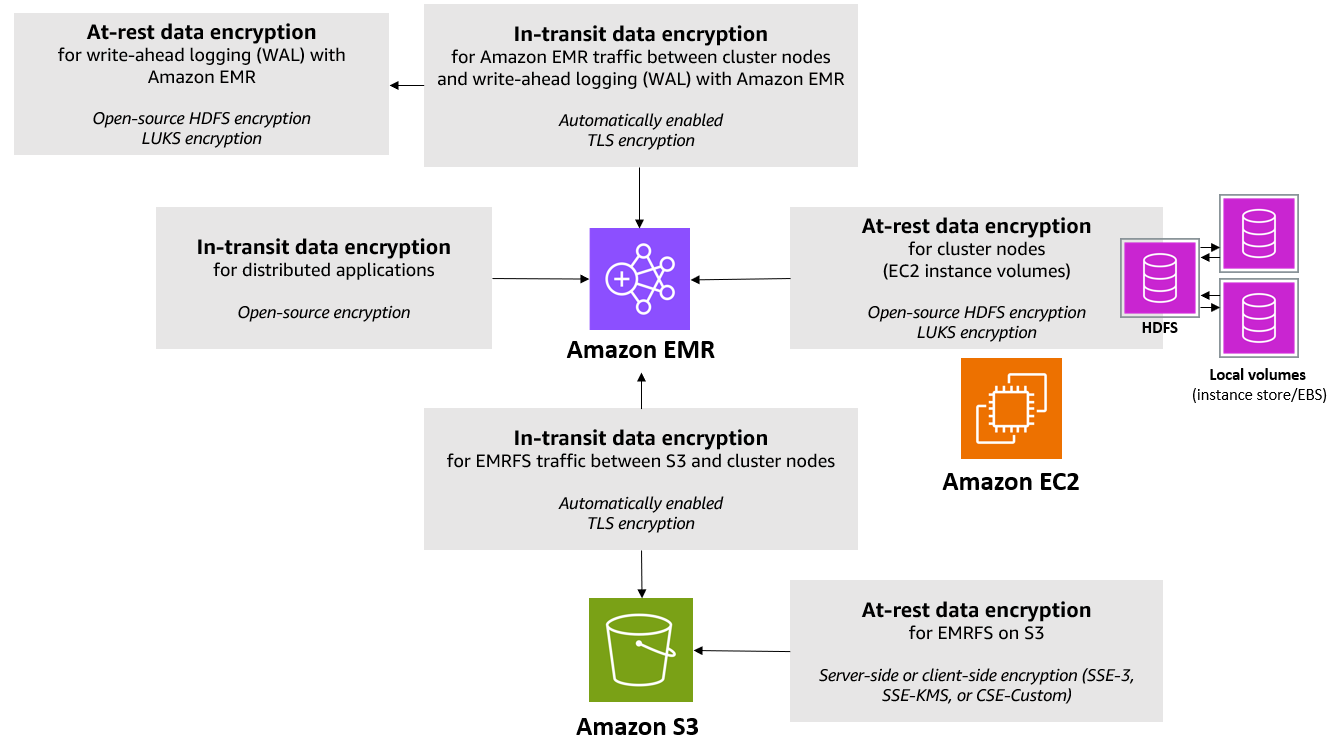
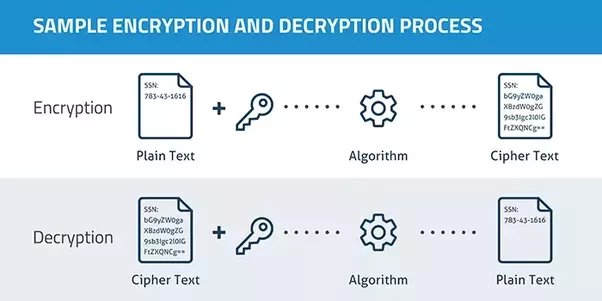
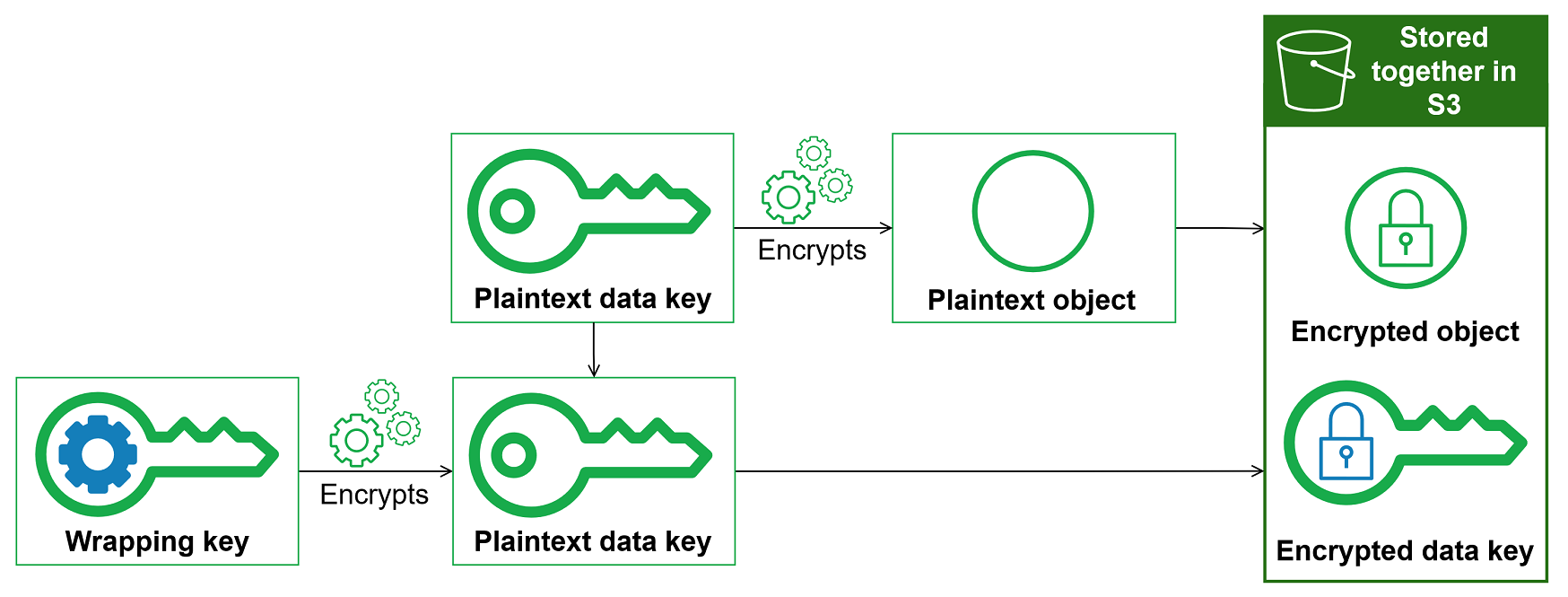
Using the AWS Encryption SDK for multiple master key encryption - SDD402 - AWS re:Inforce 2019 | PPT

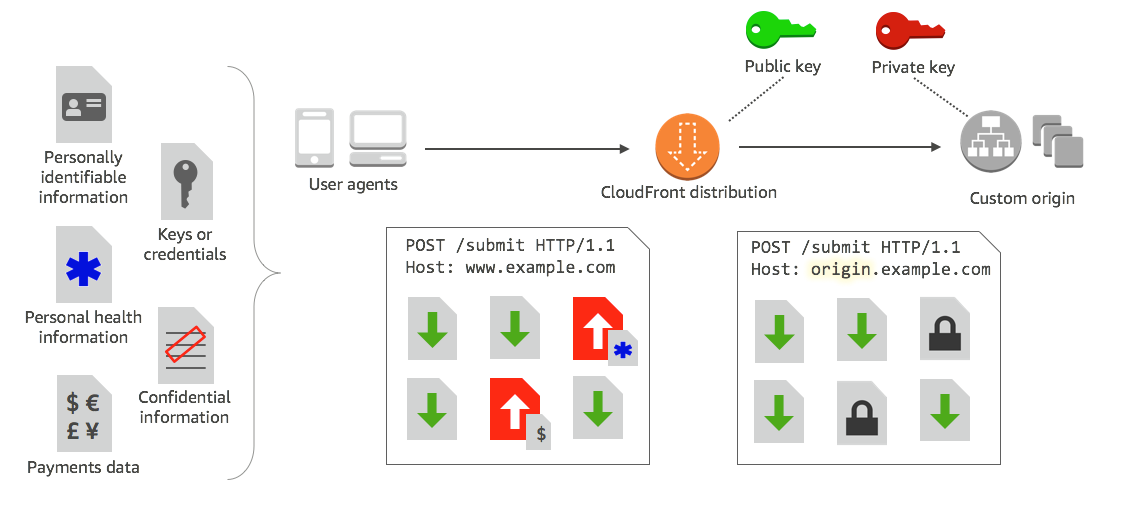
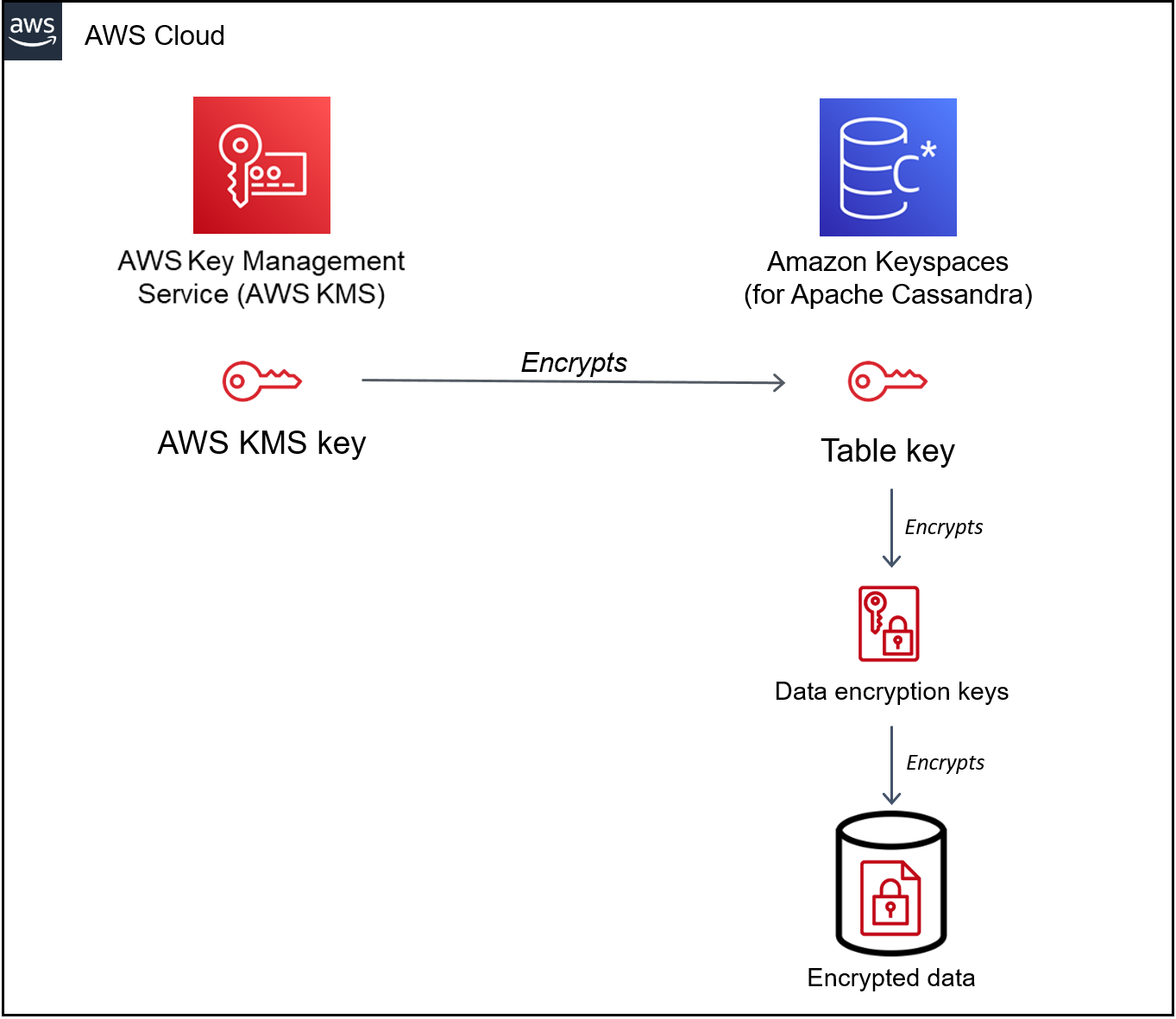
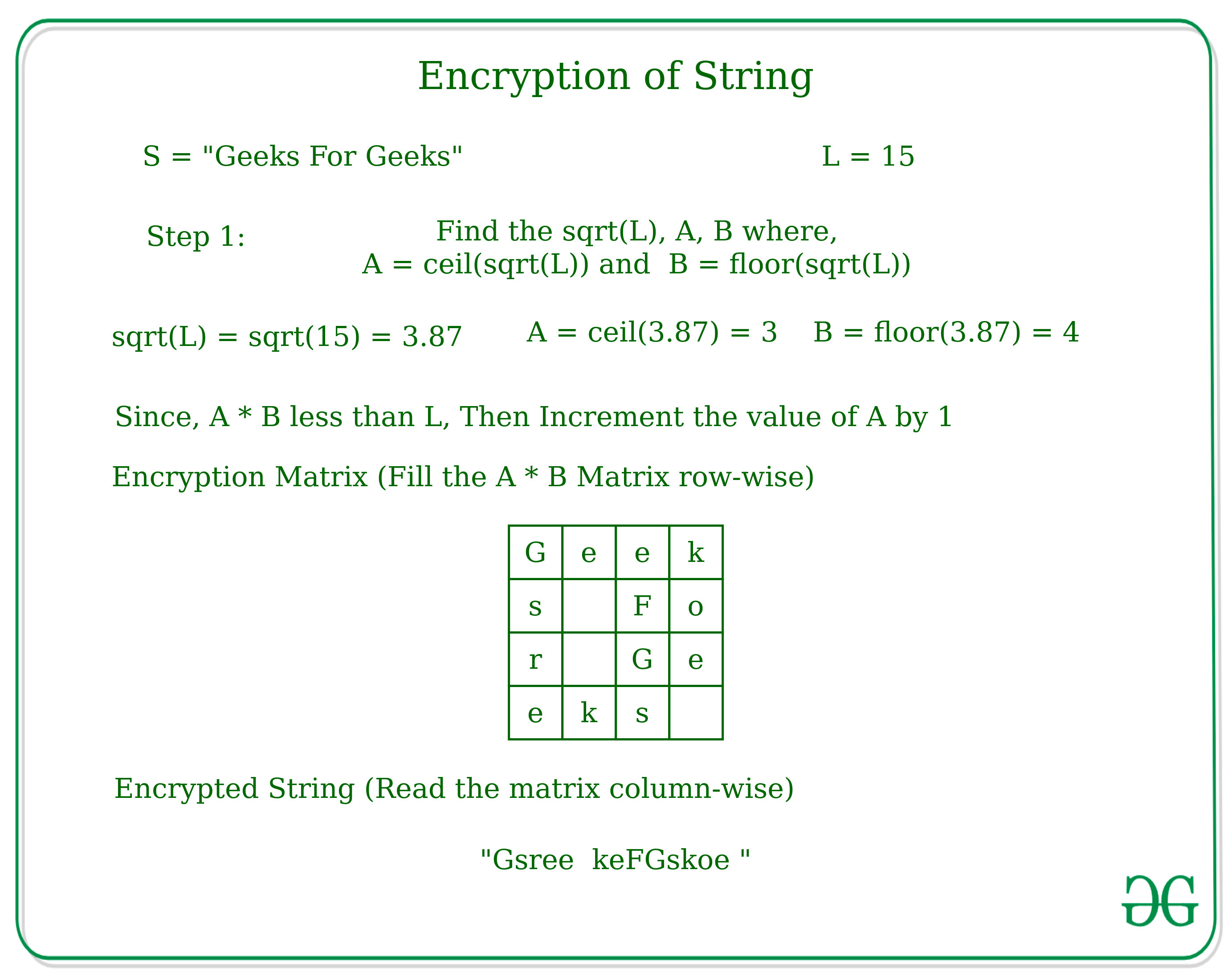
Implement column-level encryption to protect sensitive data in Amazon Redshift with AWS Glue and AWS Lambda user-defined functions | AWS Big Data Blog
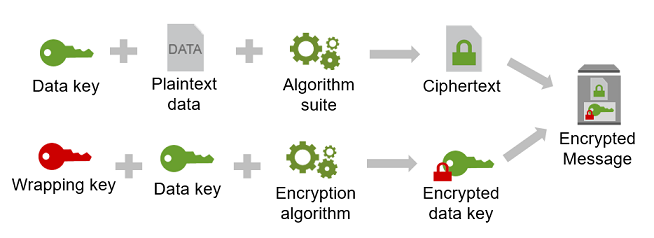
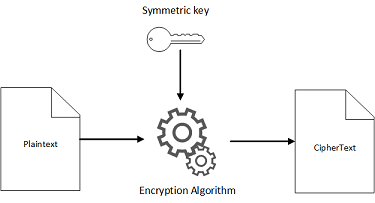
KMS and Envelope Encryption Explained | by Juan Carlos Garzon | iCapital Network Technology Group | Medium
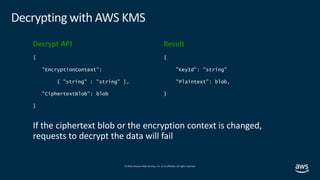
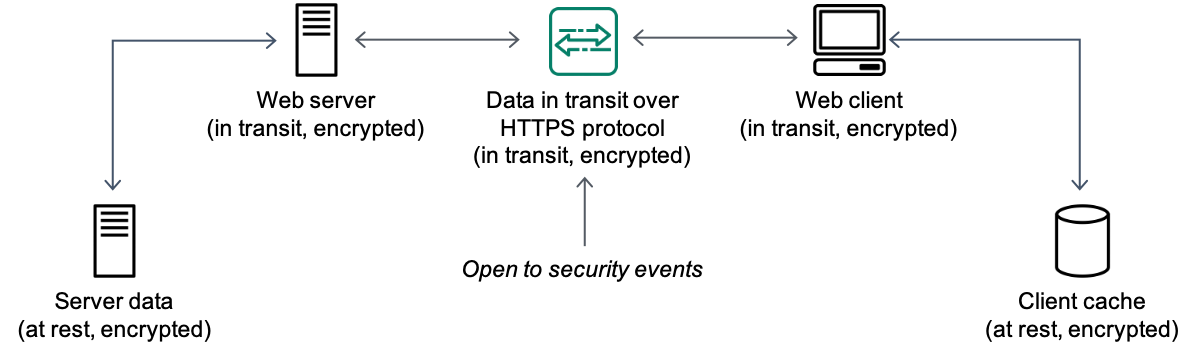
Using the AWS Encryption SDK for multiple master key encryption - SDD402 - AWS re:Inforce 2019 | PPT
Cannot decrypt message from Amazon Connect using RawRsaKeyringNode · Issue #373 · aws/aws-encryption-sdk-javascript · GitHub