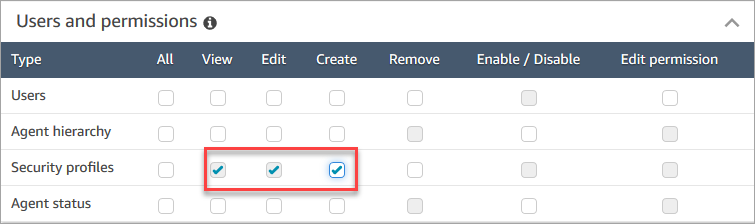
Federate access to Amazon Redshift using the JDBC browser plugin for Single Sign-on authentication with Microsoft Azure Active Directory | AWS Big Data Blog

Set up federated access to Amazon Athena for Microsoft AD FS users using AWS Lake Formation and a JDBC client | AWS Big Data Blog

Integrate Amazon Redshift native IdP federation with Microsoft Azure AD and Power BI | AWS Big Data Blog

Secure your data with Amazon RDS for SQL Server: A guide to best practices and fortification | AWS Database Blog

Integrate Amazon Redshift row-level security with Amazon Redshift native IdP authentication | AWS Big Data Blog

Secure your data with Amazon RDS for SQL Server: A guide to best practices and fortification | AWS Database Blog

Setting up trust between ADFS and AWS and using Active Directory credentials to connect to Amazon Athena with ODBC driver | AWS Big Data Blog

How AWS Managed Microsoft AD Helps to Simplify the Deployment and Improve the Security of Active Directory–Integrated .NET Applications | AWS Security Blog